PDF preview loads on demand to keep the homepage fast.
Waris Damkham
Offensive Security Engineer & AI Security Engineer
Red Teaming • AI Security • Web/AppSec

About Me
I am an Offensive Security Engineer and AI Security Engineer with hands-on experience across enterprise penetration testing and applied AI and security research. I deliver end-to-end assessments across Web, API, Mobile, and Network environments, and contribute to Red Team operations focused on real-world attack scenarios, identity abuse, and security posture improvement. My work also includes security automation, critical vulnerability response support, and AI security readiness for AI-enabled applications. I conduct applied identity and access security work on Microsoft 365 Conditional Access policy enforcement, with tooling accepted for Black Hat Asia 2026 (Arsenal) and DEF CON Singapore 2026 (Demo Labs). Open to global opportunities in Red Teaming, AI Security, and Application Security.
Experience


Key Responsibilities:
- Delivered 38 penetration tests across annual assessments and major-change projects, and contributed as a core member of advanced Red Team engagements, translating findings into remediation actions.
- Acted as project owner for 12 major security assessment projects in 2025 - 2026, leading end-to-end execution and reporting.
- Produced 30+ executive and technical summaries and delivered 24 security briefings (18 Penetration Testing: 15 Thai / 3 English; 6 Red Team), aligning stakeholders on risk impact, priorities, and action plans.
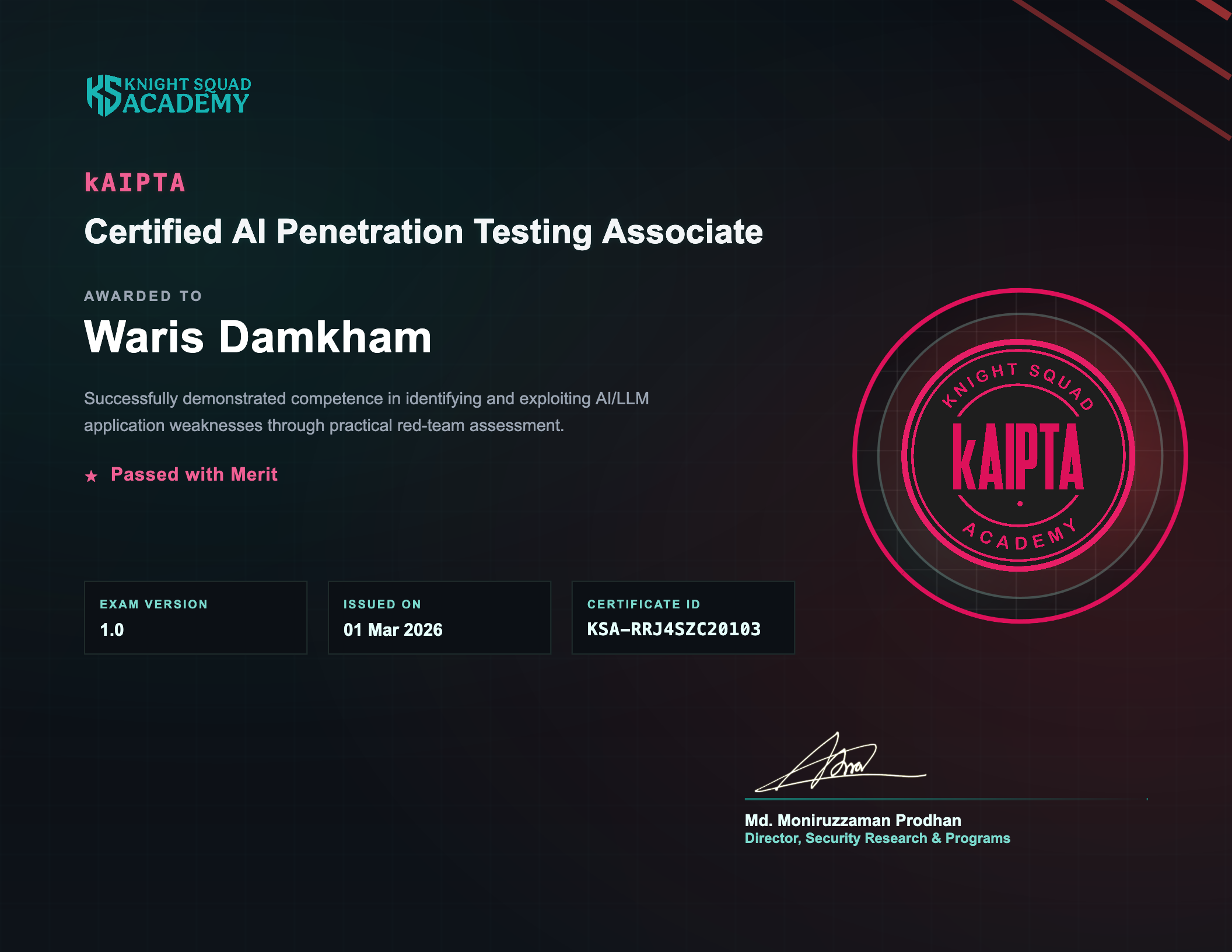
- Led AI pentesting and AI security workstreams across readiness, research, and automation tooling, using OWASP LLM Top 10 to translate emerging risks into actionable guidance and presentation-ready materials
- Led PwnDoc-ng implementation, achieving 50% reduction in operational effort and 25% reduction in review workload, and drove reporting standard upgrades through 2025 report redesign and issue write-up rewrites aligned with modern security standards.
- Built security automation to scale recurring operations, including monthly subsidiary reporting extraction (34.7% manual-effort reduction), email-driven Critical CVE follow-up (≥ 50% time reduction and ≥ 80% mitigation artifact tracking), and BitSight WAS daily scan automation supporting a BitSight rating of 800.
- Shared AI threat insights via internal briefings and knowledge-sharing sessions across regional teams.
- Designed and authored an official challenge for NCSA AI CTF (Thailand’s first Cyber AI CTF) as KBTG representative, focusing on AI security and prompt-attack scenarios.
Skills: Penetration testing · Kali Linux · Burp Suite · AI Security · Reporting · Power Automate · Power Apps


Key Responsibilities:
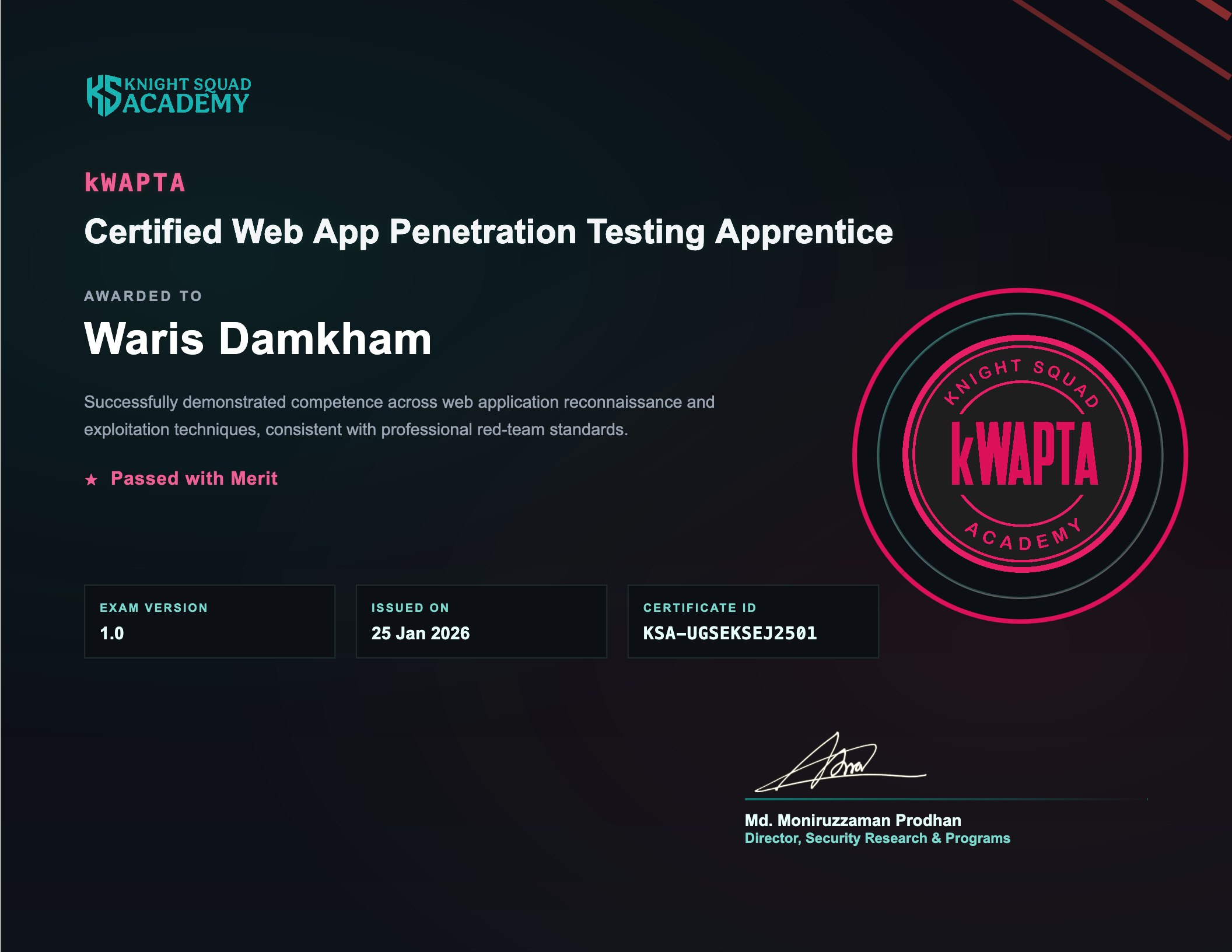
- Conducted in-depth penetration testing of IT infrastructure, identifying vulnerabilities in operating systems, applications, configurations, and user behavior.
- Specialized in web, mobile, and software vulnerability assessments following OWASP Top 10 and industry best practices.
- Delivered detailed security reports with actionable remediation steps to strengthen clients’ overall security posture.
- Worked cross-functionally with development and infrastructure teams to ensure timely remediation of security risks.
- Successfully completed 16 security assessment projects during the engagement.
Skills: Penetration testing · Kali Linux · Burp Suite · OWASP · Vulnerability Assessment


Key Responsibilities:
- Assisted in conducting penetration tests on software, mobile, and web applications using tools such as Kali Linux and Burp Suite.
- Followed OWASP best practices to identify and document security vulnerabilities and simulate real-world cyberattacks.
- Performed vulnerability assessments on KPMG’s internal network using Nessus and other scanning tools.
- Contributed to the development of a secure internal website, incorporating security-by-design principles.
- Completed 2 penetration testing projects and 1 vulnerability assessment project, improving communication of complex findings to stakeholders.
- Gained practical expertise in offensive security while actively pursuing continuous learning in a dynamic threat landscape.
Skills: Penetration testing · Kali Linux · Burp Suite · OWASP · Vulnerability Assessment

Key Responsibilities:
- Conducted research on OAuth 2.0 implementations in Android applications and browser extensions, focusing on vulnerabilities related to Cross-Site Request Forgery (CSRF).
- Evaluated critical security parameters such as the state value and authorization code to determine resilience against CSRF attacks.
- Developed a custom Android application and analyzed real-world apps and extensions to assess OAuth integration practices.
- Identified insecure implementations that exposed users to potential token hijacking and session fixation risks
- Contributed to the development of a benchmark for future security audits of Android apps and browser extensions using OAuth 2.0, promoting safer authentication design.
- Presented research findings at the Workshop on Cyber Forensics, Security, and E-discovery, part of the 23rd IEEE International Conference on Software Quality, Reliability, and Security (QRS 2023).
Skills: Android Development · OAuth2.0 · Application Security · Security · Cybersecurity · Java


Key Responsibilities:
- Contributed to a research project focused on automated COVID-19 diagnosis using deep learning and chest X-ray images.
- Developed and evaluated a convolutional neural network (CNN) model enhanced by transfer learning for accurate COVID-19 screening.
- Utilized Grad-CAM visualizations to interpret model predictions and enhance explainability for medical practitioners.
- Conducted experiments on publicly available datasets to assess model performance in terms of accuracy, precision, recall, and F-measure.
- Demonstrated expertise in artificial intelligence, deep learning, and medical image analysis applied to real-world health challenges.
- Published research findings at the 2022 6th International Conference on Information Technology (InCIT).
Skills: Public Speaking · Jupyter · Convolutional Neural Networks (CNN) · Deep Learning · Artificial Intelligence (AI) · Communication · Python
News Conference Paper Show Credential Conference Certifications
Security Vulnerabilities (CVEs)
CVE-2026-2020
JS Archive List
The JS Archive List plugin for WordPress is vulnerable to PHP Object Injection in all versions up to, and including, 6.1.7 via the 'included' shortcode attribute. This is due to the deserialization of untrusted input supplied via the 'included' parameter of the plugin's shortcode. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject a PHP Object. No known POP chain is present in the vulnerable software. If a POP chain is present via an additional plugin or theme installed on the target system, it could allow the attacker to delete arbitrary files, retrieve sensitive data, or execute code.
CVE-2026-1720
WowOptin: Next-Gen Popup Maker – Create Stunning Popups and Optins for Lead Generation
The WowOptin: Next-Gen Popup Maker – Create Stunning Popups and Optins for Lead Generation plugin for WordPress is vulnerable to unauthorized arbitrary plugin installation due to a missing capability check on the 'install_and_active_plugin' function in all versions up to, and including, 1.4.24. This makes it possible for authenticated attackers, with Subscriber-level access and above, to install and activate arbitrary plugins.
CVE-2026-1236
Envira Gallery for WordPress
The Envira Gallery for WordPress plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'justified_gallery_theme' parameter in all versions up to, and including, 1.12.3 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Author-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Talks & Contributions
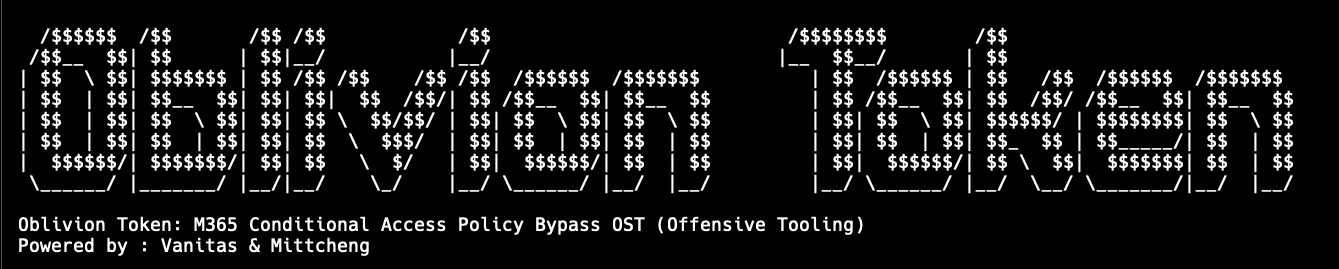
Oblivion Token: M365 Conditional Access Policy Bypass OST (Offensive Tooling)
DEF CON Singapore 2026 Demo Labs
Accepted for DEF CON Singapore 2026 Demo Labs. Oblivion Token is an offensive research utility for practical, repeatable testing of Microsoft 365 Conditional Access (CA) edge cases. It systematizes token-centric workflows to help identify where device, network, or app-context assumptions can fail in real-world environments.
Oblivion Token: M365 Conditional Access Policy Bypass OST (Offensive Tooling)
Black Hat Asia Arsenal 2026
Accepted for Black Hat Asia 2026 Arsenal. Oblivion Token is an offensive research utility for practical, repeatable testing of Microsoft 365 Conditional Access (CA) edge cases. It systematizes token-centric workflows to help identify where device, network, or app-context assumptions can fail in real-world environments.
NCSA AI CTF 2026 (Thailand) – Challenge Author
NCSA AI CTF (Thailand’s first Cyber AI CTF)
Contributed as a challenge author for NCSA AI CTF 2026, representing KBTG, focusing on AI security and prompt-injection scenarios.
Academic Publications
Research papers presented at international IEEE conferences
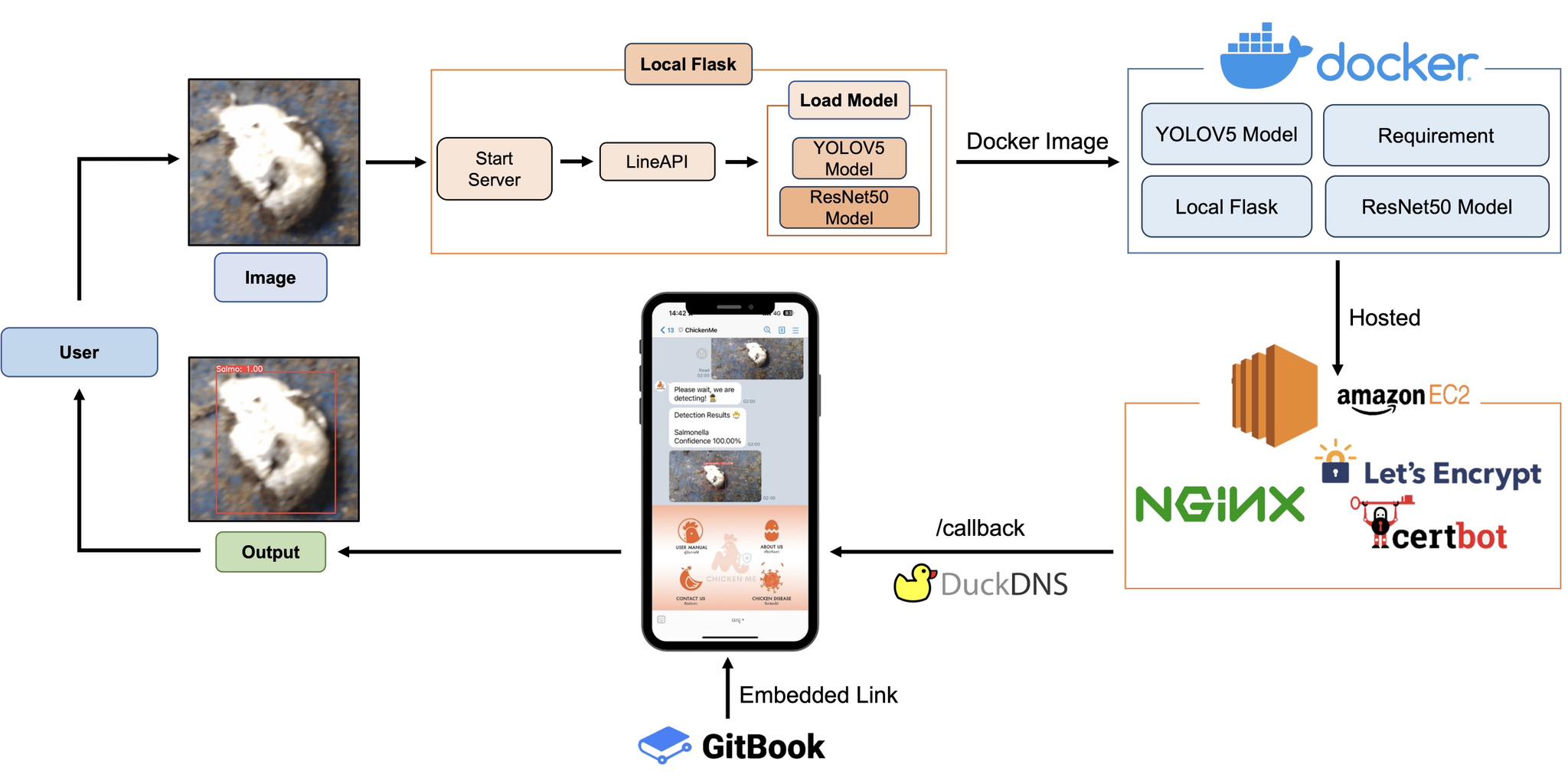
Practical Mobile Based Services for Identification of Chicken Diseases From Fecal Images
IEEE Region 10 Conference 2024
Poultry farming is crucial to the food chain, and chicken health directly impacts product quality and safety. Diagnosing poultry diseases using polymerase chain reaction is costly, particularly for small farms. To address this, we developed a mobile-based service for farmers, enabling the identification of common chicken diseases from fecal images via a Line account. Our system achieved 86.49% segmentation precision and 95.93% classification accuracy on a large dataset, offering a practical and accessible tool for local farmers.
Detecting Vulnerable OAuth 2.0 Implementations in Android Applications
23rd IEEE International Conference on Software Quality, Reliability, and Security
OAuth 2.0, commonly used for authorization, can be susceptible to CSRF attacks in Android applications. To address this, we developed an Android app to assess other apps' use of the OAuth 2.0 state parameter—a key defense against CSRF. Our analysis, conducted on both Chrome and the default browser, evaluates whether Android apps using OAuth 2.0 are adequately protected against CSRF attacks. Our research aims to protect users by highlighting apps with potentially vulnerable OAuth 2.0 implementations.
Automated COVID-19 Screening Framework Using Deep CNN With Chest X-Ray Medical Images
6th International Conference on Information Technology
An automated COVID-19 screening framework using chest X-ray images is proposed in this study. It leverages artificial intelligence techniques and transfer learning for accurate diagnosis. The framework extracts features using transfer learning and applies modified deep neural networks. Grad-CAM visualization supports the predicted diagnosis. Experimental results demonstrate superior performance compared to other deep learning techniques. This framework has the potential to aid in early COVID-19 diagnosis and alleviate the burden on radiologists.
Projects
Skills & Tools
Certifications
Education

Activities and societies:

Activities and societies:
Activities and societies:
Competitions
Blog
My Resume
waris_m@portfolio:~$ cat contact.txt
# CONTACT INFORMATION
# SOCIAL NETWORKS
waris_m@portfolio:~$


















.png)





